Comprehensive analysis of the IT infrastructure based on a detailed catalog of questions.
Cyber Security Assesment


Attack simulation - Pentest Lite
Pentesting for the effective identification of vulnerabilities.
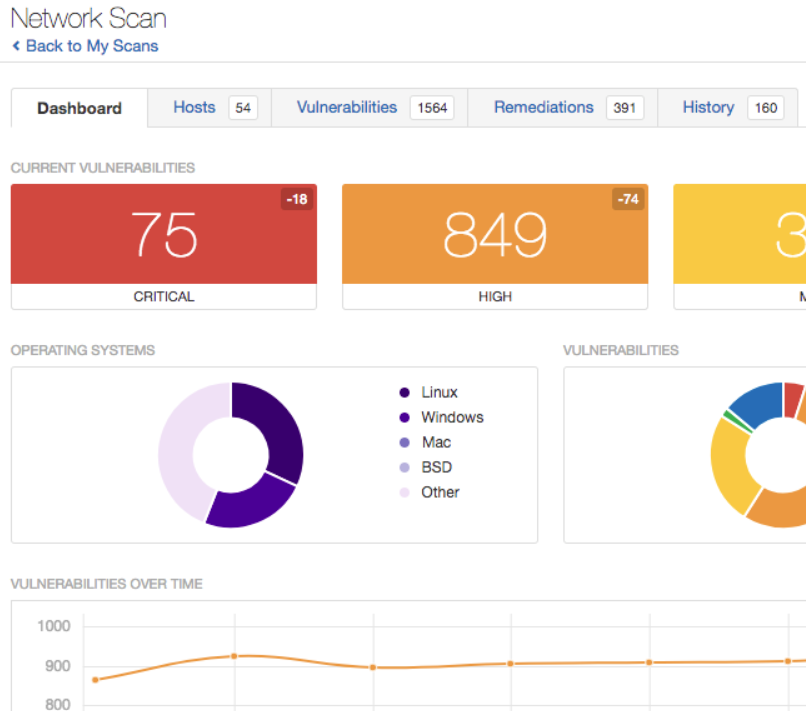
WebApp Vulnerability Check
Security check for defined web applications to identify and assess risks.
Report
Once the cyber security assessment has been completed, we prepare a detailed report
that is clear and easy to understand..
This report contains:
• An executive summary summarising the most important findings for the
management level.
• An overview of all identified vulnerabilities, categorised according to
their criticality.
• A detailed description of each vulnerability with recommendations on how
to fix it.
Cyber Security Assessment
Our security experts have experience in conducting complex audits and assessments for customers from a wide range of industries. We work closely and purposefully with you to improve your IT security through our Cyber Security Assessment, which is divided into three modules.
- 1. Audit
- 2. Attack simulation - Pentest Lite
- 3. WebApp Vulnerability Check
Conducting a comprehensive theoretical analysis of the entire IT infrastructure using a detailed catalogue of questions based on the IT baseline protection modules of the BSI and the NIST standards. The IT systems, networks, security measures, guidelines and processes are examined and analysed.
A compact version of a full penetration test that aims to identify vulnerabilities in systems in an effective but less costly way.
Conducting a Webapp Vuln Check for defined web applications to identify and evaluate security risks..